已有帐户?
需要帐户? 创建帐户已选国家/地区:Mainland China -
从机器人strongSwan的IKEv2到与EAP和RSA验证的Cisco IOS已更新: 2016 年 1 月 21 日文档 ID:116837关于翻译 目录简介先决条件要求使用的组件配置网络图证书登记Cisco IOS 软件机器人EAP 身份验证EAP验证的Cisco IOS软件配置EAP验证的机器人配置EAP验证测验RSA验证RSA验证的Cisco IOS软件配置RSA验证的机器人配置RSA验证测验在strongSwan的NAT -和Cisco IOS软件限制后的VPN网关验证故障排除strongSwan CA多个CERT_REQ在DVTI的隧道源Cisco IOS软件Bug和增强请求相关信息 简介本文描述如何配置移动版本strongSwan为了通过互联网密钥交换版本2 (IKEv2)协议访问Cisco IOS软件VPN网关。 提交三示例:
Cisco IOS软件和strongSwan限制也包括。 先决条件要求Cisco 建议您了解以下主题:
使用的组件本文档中的信息基于以下软件和硬件版本:
本文档中的信息都是基于特定实验室环境中的设备编写的。本文档中使用的所有设备最初均采用原始(默认)配置。如果您使用的是真实网络,请确保您已经了解所有命令的潜在影响。 配置网络图机器人strongSwan设立一个IKEv2通道以Cisco IOS软件网关为了安全地访问内部网络。 证书登记证书是一个前提对于基于EAP的和基于RSA的验证。 在EAP验证方案中,证书在VPN网关仅必要。客户端连接对Cisco IOS软件,只有当软件提交在机器人委托Certificate Authority (CA)时签字的一证书。EAP会话然后开始为了客户端能验证到Cisco IOS软件。 对于基于RSA的验证,两个终端必须有一正确证书。 当IP地址使用作为a peer-id时,有证书的另外的需求。如果VPN网关的IP地址在x509分机主题替代方案名称,包括机器人strongSwan验证。否则,机器人切连接;这是良好的做法以及RFC 6125的建议。 因为Cisco IOS软件有一个限制, Openssl使用作为CA :它不能生成与包括IP地址的分机的证书。所有证书由Openssl生成并且导入对机器人和Cisco IOS软件。 在Cisco IOS软件里,主题alt NAME命令可以用于为了创建包括IP地址的分机,但是命令仅运作与自签名证书。Cisco Bug ID CSCui44783, “IOS ENH PKI能力生成与主题alt NAME分机的CSR”,是增强请求允许Cisco IOS软件生成登记的所有类型的分机。 这是生成CA:命令的示例 #generate key openssl genrsa -des3 -out ca.key 2048 #generate CSR openssl req -new -key ca.key -out ca.csr #remove protection cp ca.key ca.key.org openssl rsa -in ca.key.org -out ca.key #self sign certificate openssl x509 -req -days 365 -in ca.csr -signkey ca.key -out ca.crt -extensions v3_req -extfile conf_global.crt是配置文件。应该设置CA分机为特鲁: [ req ] default_bits = 1024 # Size of keys default_md = md5 # message digest algorithm string_mask = nombstr # permitted characters #string_mask = pkix # permitted characters distinguished_name = req_distinguished_name req_extensions = v3_req [ v3_req ] basicConstraints = subjectKeyIdentifier = hash 生成证书的命令为Cisco IOS软件和机器人是非常类似的。此示例假设,已经有用于的CA签署证书: #generate key openssl genrsa -des3 -out server.key 2048 #generate CSR openssl req -new -key server.key -out server.csr #remove protection cp server.key server.key.org openssl rsa -in server.key.org -out server.key #sign the cert and add Alternate Subject Name extension from conf_global_cert.crt file with configuration openssl x509 -req -in server.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out server.crt -days 365 -extensions v3_req -extfile #create pfx file containig CA cert and server cert openssl pkcs12 -export -out server.pfx -inkey server.key -in server.crt -certfile ca.crt conf_global_cert.crt是配置文件。备选主题名称分机是关键设置。在本例中, CA分机设置对错误: [ req ] default_bits = 1024 # Size of keys default_md = md5 # message digest algorithm string_mask = nombstr # permitted characters #string_mask = pkix # permitted characters distinguished_name = req_distinguished_name req_extensions = v3_req [ v3_req ] basicConstraints = subjectKeyIdentifier = hash = @alt_names [alt_names] IP.1 = 应该为Cisco IOS软件和机器人生成证书。 IP地址10.48.64.15属于Cisco IOS软件网关。当您生成Cisco IOS软件的时一证书,请确保subjectAltName设置为10.48.64.15。机器人验证从Cisco IOS软件接收的证书并且设法查找其在subjectAltName的IP地址。 Cisco IOS 软件Cisco IOS软件需要有为基于RSA的和基于EAP的验证安装的一正确证书。 是pkcs12容器)的pfx文件(Cisco IOS软件的可以导入: BSAN-2900-1(config)# % Importing pkcs12... Source filename [server.pfx]? CRYPTO_PKI: Imported PKCS12 file successfully. 请使用verbose命令显示crypto pki的证书为了验证导入成功: BSAN-2900-1# Certificate Status: Available Version: 3 Certificate Serial Number (hex): 00A003C5DCDEFA146C Certificate Usage: General Purpose Issuer: cn=Cisco ou=Cisco TAC o=Cisco l=Krakow st=Malopolskie c=PL Validity Date: start date: 18:04:09 UTC Aug 1 2013 end date: 18:04:09 UTC Aug 1 2014 Subject Key Info: Public Key Algorithm: rsaEncryption RSA Public Key: (2048 bit) Signature Algorithm: SHA1 with RSA Encryption Fingerprint MD5: 2C45BF10 0BACB98D 444F5804 1DC27ECF Fingerprint SHA1: 26B66A66 DF5E7D6F 498DD653 A2C164D7 4C7A7F8F X509v3 extensions: X509v3 Subject Key ID: AD598A9B 8AB6893B AB3CB8B9 28B2039C 78441E72 X509v3 Basic Constraints: Authority Info Access: Associated Trustpoints: TP Storage: nvram:Cisco#146C.cer Key Label: TP Key storage device: private config CA Certificate Status: Available Version: 3 Certificate Serial Number (hex): 00DC8EAD98723DF56A Certificate Usage: General Purpose Issuer: cn=Cisco ou=Cisco TAC o=Cisco l=Krakow st=Malopolskie c=PL Subject: cn=Cisco ou=Cisco TAC o=Cisco l=Krakow st=Malopolskie c=PL Validity Date: start date: 16:39:55 UTC Jul 23 2013 end date: 16:39:55 UTC Jul 23 2014 Subject Key Info: Public Key Algorithm: rsaEncryption RSA Public Key: (2048 bit) Signature Algorithm: SHA1 with RSA Encryption Fingerprint MD5: 0A2432DC 33F0DC46 AAB23E26 ED474B7E Fingerprint SHA1: A50E3892 ED5C4542 FA7FF584 DE07B6E0 654A62D0 X509v3 extensions: X509v3 Subject Key ID: 786F263C 0F5A1963 D6AD18F8 86DCE7C9 0185911E X509v3 Basic Constraints: Authority Info Access: Associated Trustpoints: TP Storage: nvram:Cisco#F56ACA.cer BSAN-2900-1# Interface IP-Address OK? Method Status Protocol YES NVRAM up up 机器人对于基于EAP的验证, Andorid需要有安装的正确CA证书。 对于基于RSA的验证, Andorid需要有安装的CA证书和其自己的证书。 此步骤描述如何安装两证书: 这时,用户证书以及CA证书安装。pfx文件是有用户证书和CA证书的一个pkcs12容器。 当证书导入时,机器人有准确的需求。例如,对于将顺利地导入的CA证书,机器人要求x509v3分机基本限制条件CA设置为特鲁。因此,当您生成CA或使用您自己的CA时,验证是重要的它有正确分机: pluton custom_ca # openssl x509 -in ca.crt -text Certificate: Data: Version: 3 (0x2) Serial Number: dc:8e:ad:98:72:3d:f5:6a Signature Algorithm: sha1WithRSAEncryption Issuer: C=PL, ST=Malopolskie, L=Krakow, O=Cisco, OU=Cisco TAC, CN=Cisco <.....output omitted> <.....output omitted> EAP 身份验证EAP验证的Cisco IOS软件配置IKEv2允许使用EAP协议栈为了进行用户认证。VPN网关提交自己与证书。一旦客户端委托该证书,客户端响应对从网关的EAP请求标识。Cisco IOS软件用途标识和传送RADIUS请求信息到验证、授权和统计(AAA)服务器,并且EAP-MD5会话建立在请求方(机器人)和认证服务器之间(访问控制服务器[ACS]或ISE)。 在成功的EAP-MD5验证以后,如表示的是由RADIUS接受消息, Cisco IOS软件使用配置模式为了推送IP地址对客户端和继续流量选择器协商。 注意机器人发送IKEID=cisco (如配置)。在Cisco IOS软件匹配'ikev2配置文件接收的此IKEID PROF。
aaa new-model aaa authentication login aaa authorization network IKE2_AUTHOR_LOCAL local crypto pki trustpoint TP revocation-check none crypto ikev2 authorization policy IKE2_AUTHOR_POLICY pool POOL ! crypto ikev2 proposal ikev2-proposal encryption aes-cbc-128 integrity sha1 group 14 ! crypto ikev2 policy ikev2-policy proposal ikev2-proposal ! ! crypto authentication authentication pki trustpoint TP aaa authorization group eap list IKE2_AUTHOR_LOCAL IKE2_AUTHOR_POLICY aaa authorization user eap cached virtual-template 1 crypto ipsec transform-set 3DES-MD5 esp-aes esp-sha-hmac mode tunnel ! crypto ipsec profile PROF set transform-set 3DES-MD5 set ikev2-profile PROF interface GigabitEthernet0/0 ip address 10.48.64.15 255.255.255.128 interface Virtual-Template1 type tunnel ip unnumbered GigabitEthernet0/0 tunnel mode ipsec ipv4 tunnel protection ipsec profile PROF ip local pool POOL 192.168.0.1 192.168.0.10 radius-server host 10.48.66.185 key cisco EAP验证的机器人配置机器人strongSwan必须有配置的EAP : EAP验证测验在Cisco IOS软件里,这些是EAP验证的最重要的调试。多数输出为了清晰省略: debug crypto ikev2 error debug crypto ikev2 internal debug radius authentication debug radius verbose IKEv2:New ikev2 sa request admitted IKEv2:(SA ID = 1):Searching policy based on peer's IKEv2:(1): IKEv2:Sending certificates as X509 certificates RADIUS(00000025): Send Access-Request to 10.48.66.185:1645 id 1645/4,len 110 RADIUS: Received from id 1645/4 10.48.66.185:1645, Access-Challenge, len 79 RADIUS(00000025): Send Access-Request to 10.48.66.185:1645 id 1645/5,len 141 RADIUS: Received from id 1645/5 10.48.66.185:1645, Access-Challenge, len 100 RADIUS(00000025): Send Access-Request to 10.48.66.185:1645 id 1645/6,len 155 RADIUS: Received from id 1645/6 10.48.66.185:1645, Access-Accept, len 76 IKEv2:(SA ID = 1):SM Trace-> SA: I_SPI=AABAB198FACAAEDE R_SPI=D61F37C4DC875001 (R) MsgID = 00000004 CurState: R_PROC_EAP_RESP Event: IKEv2:IKEv2 local AAA author request for 'IKE2_AUTHOR_POLICY' IKEv2:Received group author attributes: ipv4-pool: POOL, route-accept any tag:1 distance:1 IKEv2:Allocated addr from local pool POOL IKEv2:(SA ID = 1):SM Trace-> SA: I_SPI=AABAB198FACAAEDE R_SPI=D61F37C4DC875001 (R) MsgID = 00000005 CurState: R_VERIFY_AUTH Event: %LINEPROTO-5-UPDOWN: Line protocol on 机器人日志指示: 00[DMN] Starting IKE charon daemon (strongSwan 5.1.0dr2,
Linux 3.4.0-perf-gf43c3d9, armv7l)
00[KNL] kernel-netlink plugin might require CAP_NET_ADMIN capability
00[LIB] loaded plugins: androidbridge charon android-log openssl fips-prf
random nonce pubkey pkcs1 pkcs8 pem xcbc hmac socket-default kernel-netlink
00[LIB] unable to load 9 plugin features (9 due to unmet dependencies)
00[JOB] spawning 16 worker threads
13[IKE]
13[ENC] generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) ]
13[NET] sending packet: from 10.147.24.153[45581] to 10.48.64.15[500]
(648 bytes)
11[NET] received packet: from 10.48.64.15[500] to 10.147.24.153[45581]
(497 bytes)
11[ENC] parsed IKE_SA_INIT response 0 [ SA KE No V V N(NATD_S_IP) N(NATD_D_IP)
CERTREQ N(HTTP_CERT_LOOK) ]
11[ENC] received unknown vendor ID:
43:49:53:43:4f:2d:44:45:4c:45:54:45:2d:52:45:41:53:4f:4e
11[ENC] received unknown vendor ID:
46:4c:45:58:56:50:4e:2d:53:55:50:50:4f:52:54:45:44
11[IKE] faking NAT situation to enforce UDP encapsulation
11[IKE] cert payload ANY not supported - ignored
11[IKE]
11[IKE] establishing CHILD_SA android
11[ENC] 1 [ IDi N(INIT_CONTACT) CERTREQ
CP(ADDR ADDR6 DNS DNS6) N(ESP_TFC_PAD_N) SA TSi TSr N(MOBIKE_SUP)
11[NET] sending packet: from 10.147.24.153[35564] to 10.48.64.15[4500]
(508 bytes)
10[NET] received packet: from 10.48.64.15[4500] to 10.147.24.153[35564]
(1292 bytes)
10[ENC] parsed IKE_AUTH response 1 [ V IDr CERT AUTH EAP/REQ/ID ]
10[IKE]
10[CFG] using certificate "C=PL, ST=Malopolska, L=Krakow, O=Cisco, OU=TAC,
CN=IOS"
10[CFG] using trusted ca certificate "C=PL, ST=Malopolskie, L=Krakow, O=Cisco,
OU=Cisco TAC, CN=Cisco"
10[CFG] reached self-signed root ca with a path length of 0
10[IKE]
10[IKE] (id 0x3B),
10[ENC] generating IKE_AUTH request 2 [ EAP/RES/ID ]
10[NET] sending packet: from 10.147.24.153[35564] to 10.48.64.15[4500]
(76 bytes)
09[NET] received packet: from 10.48.64.15[4500] to 10.147.24.153[35564]
(76 bytes)
09[ENC] parsed IKE_AUTH response 2 [ EAP/REQ/TLS ]
09[IKE] (id 0x59)
09[IKE]
09[ENC] generating IKE_AUTH request 3 [ EAP/RES/NAK ]
09[NET] sending packet: from 10.147.24.153[35564] to 10.48.64.15[4500]
(76 bytes)
08[NET] received packet: from 10.48.64.15[4500] to 10.147.24.153[35564]
(92 bytes)
08[ENC] parsed IKE_AUTH response 3 [ EAP/REQ/MD5 ]
08[IKE] (id 0x5A)
08[ENC] generating IKE_AUTH request 4 [ EAP/RES/MD5 ]
08[NET] sending packet: from 10.147.24.153[35564] to 10.48.64.15[4500]
(92 bytes)
07[NET] received packet: from 10.48.64.15[4500] to 10.147.24.153[35564]
(76 bytes)
07[ENC] parsed IKE_AUTH response 4 [ EAP/SUCC ]
07[IKE] , no MSK established
07[IKE] authentication of 'cisco' (myself) with EAP
07[ENC] generating IKE_AUTH request 5 [ AUTH ]
07[NET] sending packet: from 10.147.24.153[35564] to 10.48.64.15[4500]
(92 bytes)
06[NET] received packet: from 10.48.64.15[4500] to 10.147.24.153[35564]
(236 bytes)
06[ENC] parsed IKE_AUTH response 5 [ AUTH CP(ADDR) SA TSi TSr N(SET_WINSIZE)
N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) ]
06[IKE]
06[IKE]
06[IKE] scheduling rekeying in 35421s
06[IKE] maximum IKE_SA lifetime 36021s
06[IKE]
06[IKE] received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
06[IKE] CHILD_SA android{1} established with SPIs c776cb4f_i ea27f072_o and
TS 192.168.0.1/32 === 0.0.0.0/0
06[DMN] setting up TUN device for CHILD_SA android{1}
06[DMN]此示例显示如何验证在Cisco IOS软件的状态: BSAN-2900-1# Crypto session current status Code: C - IKE Configuration mode, D - Dead Peer Detection K - Keepalives, N - NAT-traversal, T - cTCP encapsulation X - IKE Extended Authentication, F - IKE Fragmentation Interface: Virtual-Access1 Uptime: 00:02:12 Session status: UP-ACTIVE Peer: 10.147.24.153 port 60511 fvrf: (none) ivrf: (none) Phase1_id: cisco Desc: (none) IKEv2 SA: local /4500 remote /60511 Active Capabilities:NX connid:1 lifetime:23:57:48 IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 host 192.168.0.2 Active SAs: 2, origin: crypto map Inbound: #pkts dec'ed 40 drop 0 life (KB/Sec) 4351537/3468 Outbound: #pkts enc'ed 5 drop 0 life (KB/Sec) 4351542/3468 BSAN-2900-1# IPv4 Crypto IKEv2 SA Tunnel-id Local Remote fvrf/ivrf Status 1 10.48.64.15/4500 10.147.24.153/60511 none/none READY Encr: AES-CBC, keysize: 128, Hash: SHA96, DH Grp:14, Life/Active Time: 86400/137 sec CE id: 1002, Session-id: 2 Status Description: Negotiation done Local spi: D61F37C4DC875001 Remote spi: AABAB198FACAAEDE Local id: 10.48.64.15 Remote id: cisco Remote EAP id: cisco Local req msg id: 0 Remote req msg id: 6 Local next msg id: 0 Remote next msg id: 6 Local req queued: 0 Remote req queued: 6 Local window: 5 Remote window: 1 DPD configured for 0 seconds, retry 0 Fragmentation not configured. Extended Authentication configured. NAT-T is detected outside Cisco Trust Security SGT is disabled Initiator of SA : No 这些图显示如何验证在机器人的状态: RSA验证RSA验证的Cisco IOS软件配置在Rivest Shamir Adelman (RSA)验证,机器人发送证书为了验证到Cisco IOS软件。所以绑定该流量对特定IKEv2配置文件的证书地图是需要的。用户EAP验证没有要求。 这是示例远端对等体的RSA验证如何设置: crypto pki certificate map CERT_MAP 10 subject-name co android crypto ikev2 profile PROF match certificate CERT_MAP authentication authentication pki trustpoint TP aaa authorization group cert list IKE2_AUTHOR_LOCAL IKE2_AUTHOR_POLICY virtual-template 1 RSA验证的机器人配置用户凭证由用户证书替换了: RSA验证测验在Cisco IOS软件里,这些是RSA验证的最重要的调试。多数输出为了清晰省略: debug crypto ikev2 error debug crypto ikev2 internal debug crypto pki transactions debug crypto pki validation debug crypto pki messages IKEv2:New ikev2 sa request admitted IKEv2:(SA ID = 1):Searching policy based on peer's identity IKEv2:(1): IKEv2:Sending certificates as X509 certificates IKEv2:(SA ID = 1):Peer's authentication method is 'RSA' IKEv2:Peer has sent X509 certificates CRYPTO_PKI: Found a issuer match CRYPTO_PKI: (9000B) Certificate is verified CRYPTO_PKI: (9000B) Certificate validation succeeded IKEv2:(SA ID = 1):[Crypto Engine -> IKEv2] Verification of signed authentication data PASSED IKEv2:IKEv2 local AAA author request for 'IKE2_AUTHOR_POLICY' IKEv2:Received group author attributes: ipv4-pool: POOL, route-accept any tag:1 distance:1 IKEv2:Allocated addr from local pool POOL IKEv2:(SA ID = 1):SM Trace-> SA: I_SPI=E53A57E359A8437C R_SPI=A03D273FC75EEBD9 (R) MsgID = 00000001 CurState: R_VERIFY_AUTH Event: %LINEPROTO-5-UPDOWN: Line protocol on 机器人日志指示: 00[DMN] Starting IKE charon daemon (strongSwan 5.1.0dr2,
Linux 3.4.0-perf-gf43c3d9, armv7l)
00[KNL] kernel-netlink plugin might require CAP_NET_ADMIN capability
00[LIB] loaded plugins: androidbridge charon android-log openssl fips-prf
random nonce pubkey pkcs1 pkcs8 pem xcbc hmac socket-default
00[LIB] unable to load 9 plugin features (9 due to unmet dependencies)
00[JOB] spawning 16 worker threads
05[CFG] loaded user certificate 'C=PL, ST=Malopolska, L=Krakow, O=Cisco,
OU=TAC, CN=android' and private key
05[CFG] loaded CA certificate 'C=PL, ST=Malopolskie, L=Krakow, O=Cisco,
OU=Cisco TAC, CN=Cisco'
05[IKE] android[4] to 10.48.64.15
05[ENC] generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) ]
05[NET] sending packet: from 10.147.24.153[34697] to 10.48.64.15[500]
(648 bytes)
10[NET] received packet: from 10.48.64.15[500] to 10.147.24.153[34697]
(497 bytes)
10[ENC] parsed IKE_SA_INIT response 0 [ SA KE No V V N(NATD_S_IP) N(NATD_D_IP)
CERTREQ N(HTTP_CERT_LOOK) ]
10[ENC] received unknown vendor ID:
43:49:53:43:4f:2d:44:45:4c:45:54:45:2d:52:45:41:53:4f:4e
10[ENC] received unknown vendor ID:
46:4c:45:58:56:50:4e:2d:53:55:50:50:4f:52:54:45:44
10[IKE] faking NAT situation to enforce UDP encapsulation
10[IKE] cert payload ANY not supported - ignored
10[IKE]
10[IKE] authentication of 'C=PL, ST=Malopolska, L=Krakow, O=Cisco, OU=TAC,
CN=android' (myself) with RSA signature successful
10[IKE] sending end entity cert "C=PL, ST=Malopolska, L=Krakow, O=Cisco,
OU=TAC, CN=android"
10[IKE] establishing CHILD_SA android
10[ENC] generating IKE_AUTH request 1 [ IDi CERT N(INIT_CONTACT) CERTREQ
AUTH CP(ADDR ADDR6 DNS DNS6) N(ESP_TFC_PAD_N) SA
10[NET] sending packet: from 10.147.24.153[44527] to 10.48.64.15[4500]
(1788 bytes)
12[NET] received packet: from 10.48.64.15[4500] to 10.147.24.153[44527]
(1420 bytes)
12[ENC] parsed IKE_AUTH response 1 [ V IDr CERT AUTH CP(ADDR) SA TSi TSr
N(SET_WINSIZE) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG)
12[IKE]
12[CFG] using certificate "C=PL, ST=Malopolska, L=Krakow, O=Cisco, OU=TAC,
CN=IOS"
12[CFG] using trusted ca certificate "C=PL, ST=Malopolskie, L=Krakow, O=Cisco,
OU=Cisco TAC, CN=Cisco"
12[CFG] reached self-signed root ca with a path length of 0
12[IKE]
12[IKE]
12[IKE] scheduling rekeying in 35413s
12[IKE] maximum IKE_SA lifetime 36013s
12[IKE]
12[IKE] received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
12[IKE] CHILD_SA android{4} established with SPIs ecb3af87_i b2279175_o and
TS 192.168.0.3/32 === 0.0.0.0/0
12[DMN] setting up TUN device for CHILD_SA android{4}
12[DMN]在Cisco IOS软件里, RSA使用签字和验证;在前一场景, EAP使用了验证: BSAN-2900-1# IPv4 Crypto IKEv2 SA Tunnel-id Local Remote fvrf/ivrf Status 1 10.48.64.15/4500 10.147.24.153/44527 none/none READY Encr: AES-CBC, keysize: 128, Hash: SHA96, DH Grp:14, Life/Active Time: 86400/16 sec CE id: 1010, Session-id: 3 Status Description: Negotiation done Local spi: A03D273FC75EEBD9 Remote spi: E53A57E359A8437C Local id: 10.48.64.15 Remote id: cn=android,ou=TAC,o=Cisco,l=Krakow,st=Malopolska,c=PL Local req msg id: 0 Remote req msg id: 2 Local next msg id: 0 Remote next msg id: 2 Local req queued: 0 Remote req queued: 2 Local window: 5 Remote window: 1 DPD configured for 0 seconds, retry 0 Fragmentation not configured. Extended Authentication not configured. NAT-T is detected outside Cisco Trust Security SGT is disabled Assigned host addr: Initiator of SA : No 在机器人的状态验证类似于那在前一场景。 在strongSwan的NAT -和Cisco IOS软件限制后的VPN网关此示例解释strongSwan证书验证的限制。 假设, Cisco IOS软件VPN网关IP地址从172.16.1.1静态翻译到10.147.25.80。使用EAP验证。 也假设Cisco IOS软件证书有一附属的替代方案名称对于172.16.1.1和10.147.25.80。 在成功的EAP验证以后,机器人进行验证并且设法查找在机器人配置对等体的IP地址(10.147.25.80)方面使用在附属的替代方案名称分机。验证发生故障: 日志指示: constraint check failed: identity '10.147.25.80' required 失败发生了,因为机器人能只读第一附属的替代方案名称分机(172.16.1.1)。 现在,假设, Cisco IOS软件证书有两个地址在附属的替代方案名称,但是在反向顺序:10.147.25.80和172.16.1.1。机器人在第三数据包执行验证,当接收IKEID时,是VPN网关(172.16.1.1)的IP地址, : 现在日志显示: no trusted RSA public key found for '172.16.1.1' 因此,当机器人接收IKEID时,它需要查找在附属的替代方案名称的IKEID,并且能使用仅第一个IP地址。 验证验证和测试程序在配置示例内是可用的。 故障排除本部分提供的信息可用于对配置进行故障排除。 strongSwan CA多个CERT_REQ当在strongSwan的证书设置是自动选择(默认),机器人在第三数据包的本地存储发送所有信任证书的CERT_REQ。因为认可很大数量的证书请求作为拒绝服务攻击, Cisco IOS软件也许下降请求: *Jul 15 07:54:13: IKEv2:number of cert req exceeds the reasonable limit (100) 在DVTI的隧道源虽然它是相当普遍的设置在一个虚拟隧道接口(VTI)的隧道源,不必要的在这里。假设tunnel source命令在一动态VTI (DVTI)下: interface Virtual-Template1 type tunnel ip unnumbered GigabitEthernet0/0 tunnel mode ipsec ipv4 tunnel protection ipsec profile PROF 在验证以后,如果Cisco IOS软件设法创建从虚拟模板被克隆的虚拟访问接口,它返回错误: *Aug 1 13:34:22 IKEv2:Allocated addr 192.168.0.9 from local pool POOL *Aug 1 13:34:22 IKEv2:(SA ID = 1):Set received config mode data *Aug 1 13:34:22 IKEv2:% DVTI create request sent for profile PROF with PSH index 1 *Aug 1 13:34:22 IKEv2: *Aug 1 13:34:24 IKEv2:Got a packet from dispatcher *Aug 1 13:34:24 IKEv2:Processing an item off the pak queue *Aug 1 13:34:24 IKEv2:Negotiation context locked currently in use 在失败以后的两秒, Cisco IOS软件接收从机器人的被重新传输的IKE_AUTH。该数据包丢弃。 Cisco IOS软件Bug和增强请求
相关信息
由思科工程师提供
此文档是否有帮助?联系我们相关的思科社区讨论
分享2012/06/07: 上传更新的XTC软件。 参考: Bria for iPad : http://bbs.feng.com/read-htm-tid-2730271-toread-1.html Acrobits Softphone: http://bbs.feng.com/read-htm-tid-1382376.html 一、准备工作: (1) 需要电脑一台,操作系统Windows 2000/XP/2003/2008/Vista/7等,内存256以上,硬盘1G以上。 (2) 需要有WiFi网络,iPhone需要支持WiFi,iPhone 4或者4S。如果没有2部iPhone,可以下载PC版的 Bria软件:http://www.3ddown.com/soft/32960.htm (3) 电脑的局域网网卡地址设置为固定IP,比如192.168.1.20等。 (4)XTC内置了号码 88880000---88880099 ,密码都是 123456 二、先配置XTC电话服务器软件: 1. 将XTC.exe拷贝到C:\根目录  XTC.rar XTC.rar  XTC.rar XTC.rar 2. 以管理员用户打开命令终端 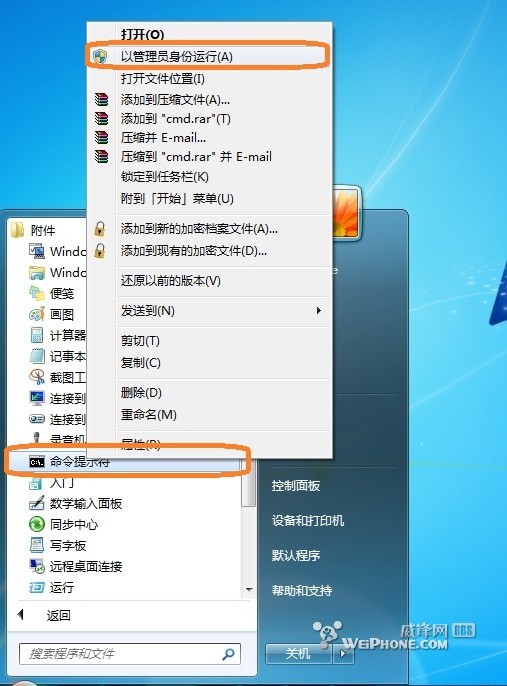 3. 执行ipconfig命令,查看本机的IP地址,最好设置成固定IP 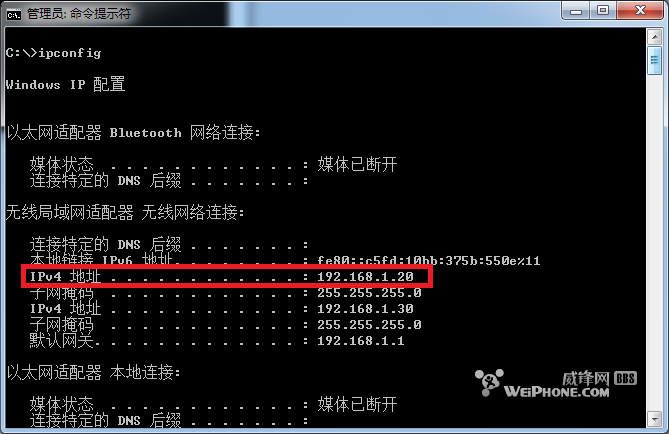 4. 将当前目录切换到c:\,然后执行 xtc -install 192.168.1.20 (这里IP地址为可选,如果不指定,XTC自动选择一个本机IP),可以看到安装已经成功 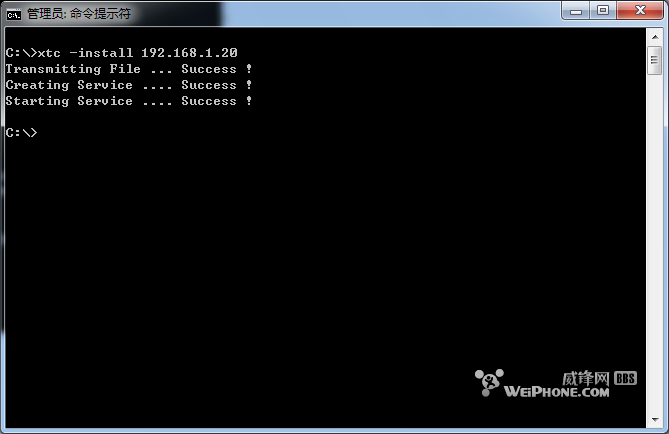 xtc 其他命令: xtc -install [IP] 安装,并启动服务,如果指定IP地址,则则XTC运行在指定的IP地址,不指定则XTC自动选择一个本机IP地址运行 xtc -remove 卸载 xtc -start [IP]启动服务,指定IP地址,则XTC运行在指定的IP地址,如果不指定则使用安装时指定的IP地址 xtc -stop 停止服务 到此,XTC电话服务器就安装完成了。 二、配置iPhone上的Softphone iPhone上的SIP协议的软电话有很多,SIP软电话的老祖宗是X-Lite,后来的商务版本是EyeBeam,再后来的Bria,一直都是最好的SIP软电话,自然少不了iPhone版本,目前的Bria for iPhone版本已经更新到2.0.3,从2.0开始已经支持视频通话,但是视频通话功能是以插件方式提供的,即购买了Bria for iPhone软件后,需要另外单独购买插件。Bria for iPhone 有三个可选插件供选择: 1. G.729 Audio Codec 语音编解码插件,该插件价格比较贵,价格已经超过Bria 软件本身,达到60元人民币。经常使用VOIP电话的人,的确可以考虑购买,带宽占用只有G.711的1/8,且音质差不了多少。 2. Presence and Messaging,状态呈现和即时消息,显示好友的状态和发送文本消息。 3. Video Calls,即视频通话功能,支持H.264一种编解码。 下载 (已破解)  Bria-iPhoneEdition-2.0.4.10863.part1.rar Bria-iPhoneEdition-2.0.4.10863.part1.rar  Bria-iPhoneEdition-2.0.4.10863.part2.rar Bria-iPhoneEdition-2.0.4.10863.part2.rar  Bria-iPhoneEdition-2.0.4.10863.part3.rar Bria-iPhoneEdition-2.0.4.10863.part3.rar  Bria-iPhoneEdition-2.0.4.10863.part4.rar Bria-iPhoneEdition-2.0.4.10863.part4.rar  Bria-iPhoneEdition-2.0.4.10863.part5.rar Bria-iPhoneEdition-2.0.4.10863.part5.rar Bria 设置选项很多,看起来很复杂,但是很专业。 |
推荐本站淘宝优惠价购买喜欢的宝贝:
本文链接:https://sg.hqyman.cn/post/448.html 非本站原创文章欢迎转载,原创文章需保留本站地址!












 反馈
反馈

 微信支付宝扫一扫,打赏作者吧~
微信支付宝扫一扫,打赏作者吧~
